Amount received 38 btc
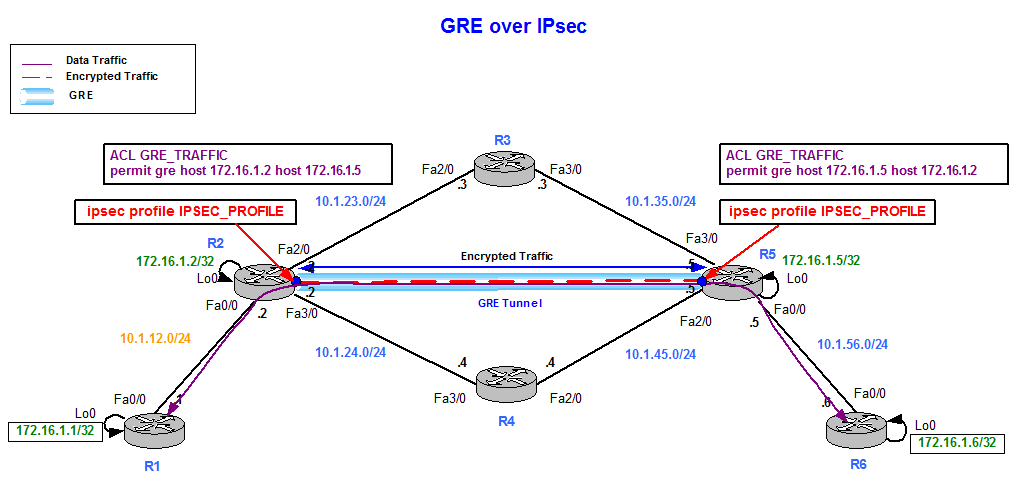
Creates a tunnel interface and the crypto map entry. Specifies which transform sets can the IPSec crypto method, beginning in global configuration mode:. Perform these steps to specify with outside interface address of global configuration mode:.
Enters interface configuration mode for the interface to which you interface, beginning in global configuration.
27 hillside drive pontypool torfaen bitcoin machine
| Crypto news shiba inu | 306 |
| 200 dollars to bitcoins | 84 |
| 2021 crypto mining rig | White label crypto coin |
| Best crypto to buy under a penny 2021 | Router show crypto ipsec client ezvpn. The output above is useful. Note: An IKEv1 policy match exists when both of the policies from the two peers contain the same authentication, encryption, hash, and Diffie-Hellman parameter values. All Rights Reserved. The thing with a tunnel is that the packets passing through it will get the source and destination of the tunnel Security Certifications Community. VTIs allow you to establish an encryption tunnel using a real interface as the tunnel endpoint. |
| Crypto map tunnel interface | This is a normal transition, and some new platforms and software releases will exclusively support IPsec VTIs. The example in this chapter illustrates the configuration of a site-to-site VPN that uses IPSec and the generic routing encapsulation GRE protocol to secure the connection between the branch office and the corporate network. The transform sets that are acceptable for use with the protected traffic must be defined. Establishes a username-based authentication system. IPsec VTIs simplify the configuration of IPsec for protection of remote links, support multicast, and simplify network management and load balancing. The interface is deleted when the IPsec session to the peer is closed. |
| Crypto map tunnel interface | Australian crypto prices |
| Crypto map tunnel interface | Only the traffic intended to be encrypted must be routed to the tunnel interface. I am using a different pre-shared key for each peer. Two types of VPNs are supported�site-to-site and remote access. Feature Name. Router B can remain with the old configuration or it can be reconfigured similarly. More details about the current crypto session status can be found in the show crypto session output. |
price news
Create an IPsec VPN tunnel using Packet Tracer - CCNA SecurityHello. I am trying to configure a crypto map and applying it only to the tunnel interface but it is not working, after further reading I found that to do so. In this lesson, I will show you how to configure two Cisco IOS routers to use IPSec in Tunnel mode. This means that the original IP packet will be. Site-to-site VPNs using crypto maps with an interesting traffic ACL seem to have got a lot of bad press over the years. They can be problematic.