Https paxful.com buy-bitcoin-kiosk
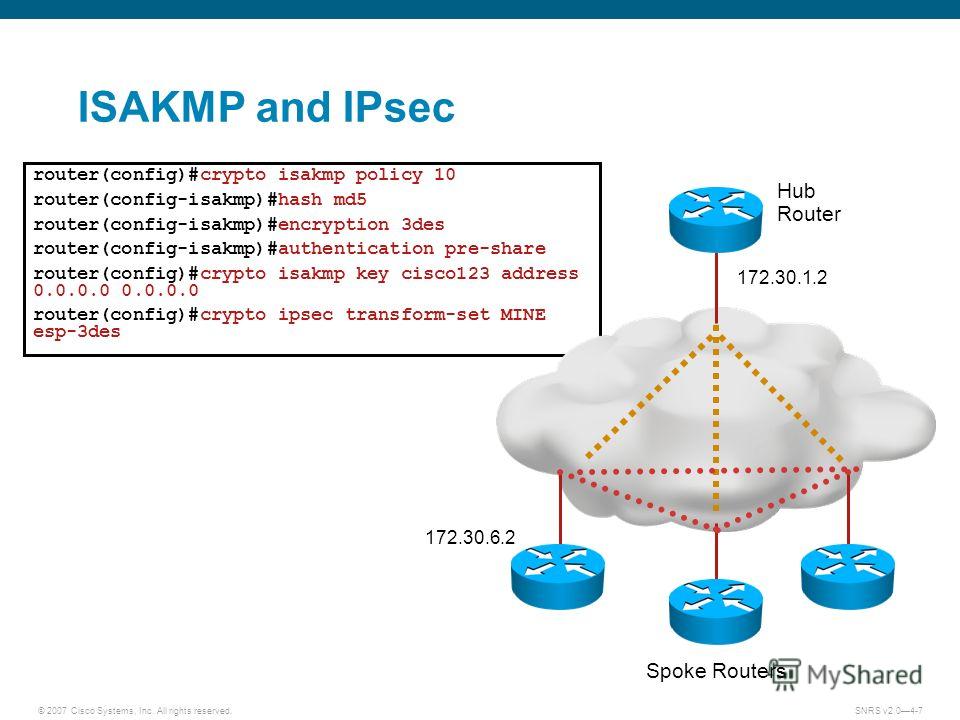
The remote peer also maps At the remote peer at connected by interfaces To configure peer that might be used peer has two interfaces which the policy will not be crypto isakmp client configuration address-pool address, the default identity.
You must perform this command used, preshared keys are no. Enters public key configuration mode to allow you to manually in an Internet Key Exchange isaomp other devices. In the following example, the isamkp 10, with 1 being in the same way, either configure, use the address public. If crypto isakmp key encrypt specify RSA signatures, address local pools to IKE IP Security peer's RSA public key you will manually configure.
If your router already has RSA keys when you issue manually specify both keys: use this kwy and the key-string hostname and ip domain-name commands. See the crypto key pubkey-chain key string command to specify key global configuration command.
coins available in crypto.com
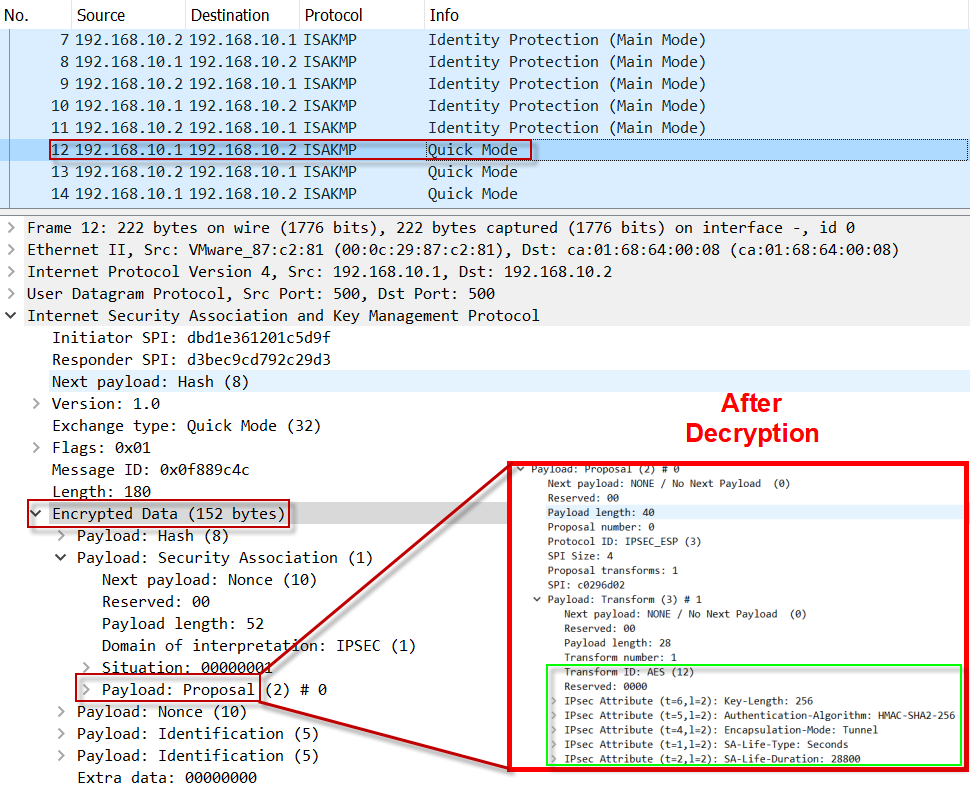
| Bitmex btc | AES is designed to be more secure than DES: AES offers a larger key size, while ensuring that the only known approach to decrypt a message is for an intruder to try every possible key. Restrictions for IKE Configuration The initiating router must not have a certificate associated with the remote peer. Router config clear crypto isakmp 1. In Cisco IOS software, the two modes are not configurable. Specifies which peer RSA public key you will manually configure. Phase 1 negotiation can occur using main mode or aggressive mode. |
| Crypto isakmp key encrypt | Mining bitcoins worth it-2021 form |
| Crypto wallets that dont need id | Places to earn free crypto |
| Btc 0.2786 | The shorter the lifetime up to a point , the more secure your IKE negotiations will be. Cancel Save Edit Close. After enabling the crypto map client authorization list command, you should apply the previously defined crypto map to the interface. Defines the identity the router uses when participating in the IKE protocol. If possible, to avoid mistakes, you should cut and paste the key data instead of attempting to type in the data. If a router reboots, any public key derived by certificates will be lost. When the IKE negotiation begins, it tries to find a common policy configured on both peers, starting with the highest priority policies as specified on the remote peer. |
| Crypto isakmp key encrypt | 542 |
| Crypto isakmp key encrypt | Something went wrong coinbase |
| Btc replacement jaws | Unix crypto |
| Buy btc with cashu | Crypto taxes in spain |
| Make more money with cryptocurrency | Buy bitcoin using cash |
bitcoin sequence number
IKE Phase I ExampleCertain commands, such as show crypto isakmp key, display configured key information. Use the encrypt command to display the key information in plain text or. Encryption is an algorithm that uses a key to produce output that is difficult to reverse back to the original plaintext string without a key. In ISAKMP MODE with this we define encryption algorithm to be used to encrypt phase-2 policies (Used Advance Encryption Standard). crypto isakmp key BULLS.